Like the Transmission Control Protocol (TCP), SNMP is an Internet protocol. Internet protocols are created by the Internet community, a group of individuals and organizations that developed and/or regularly use a large, diverse international network called the Internet. The Internet derived from the Advanced Research Projects Agency network (ARPANET), which was created by packet switching researchers in the early 1970s.
There are two versions of SNMP: Version 1 and Version 2. Most of the changes introduced in Version 2 increase SNMP's security capabilities. Other changes increase interoperability by more rigorously defining the specifications for SNMP implementation. SNMP's creators believe that after a relatively brief period of coexistence, SNMP Version 2 (SNMPv2) will largely replace SNMP Version 1 (SNMPv1). SNMP is part of a larger architecture called the Internet Network Management Framework (NMF), which is defined in Internet documents called requests for comments (RFCs). The SNMPv1 NMF is defined in RFCs 1155, 1157, and 1212, and the SNMPv2 NMF is defined by RFCs 1441 through 1452.
Today, SNMP is the most popular protocol for managing diverse commercial internetworks as well as those used in universities and research organizations. SNMP-related standardization activity continues even as vendors develop and release state-ofthe-art, SNMP-based management applications. SNMP is a relatively simple protocol, yet its feature set is sufficiently powerful to handle the difficult problems presented in trying to manage today's heterogeneous networks.
The Internet Management Model
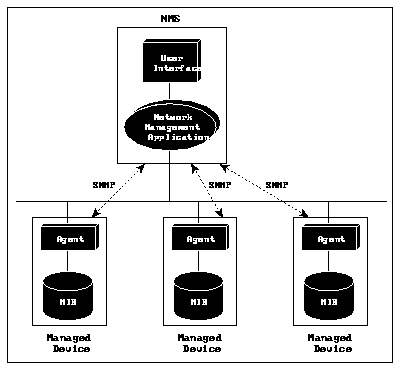
As specified in Internet RFCs and other documents, a network management system comprises:
Figure 1: The Internet Management Model
Interactions between the NMS and managed devices can be any of four different types of commands:
A MIB can be depicted as an abstract tree with an unnamed root. Individual data items make up the leaves of the tree. Object identifiers (IDs) uniquely identify or name MIB objects in the tree. Object IDs are like telephone numbers -- they are organized hierarchically with specific digits assigned by different organizations.
The object ID structure of an SNMP MIB defines three main branches: Consultative Committee for International Telegraph and Telephone (CCITT), International Organization for Standardization (ISO), and joint ISO/CCITT. Much of the current MIB activity occurs in the portion of the ISO branch defined by object identifier 1.3.6.1 and dedicated to the Internet community.
The current Internet-standard MIB, MIB-II, is defined in RFC 1213 and contains 171 objects. These objects are grouped by protocol (including TCP, IP, User Datagram Protocol [UDP], SNMP, and others) and other categories, including "system" and "interfaces."
The MIB tree is extensible by virtue of experimental and private branches. Vendors can define their own private branches to include instances of their own products. For example, Cisco's private MIB is represented by the object identifier 1.3.6.1.4.1.9. It includes objects such as "HostConfigAddr," which is identified by object ID 1.3.6.1.4.1.9.2.2.1.51. The HostConfigAddr object specifies the address of the host that provided the host configuration file for a specific Cisco device.
The basic MIB structure, including MIB-II (object ID = 1.3.6.1.2.1) and the Cisco private MIB (object ID = 1.3.6.1.4.1.9), is shown in Figure 2. A more detailed version of Cisco's private MIB is illustrated in Figure 5.
Figure 2: The Basic MIB Structure
SMI Definitions
The SMI specifies that all managed objects should have a name, a syntax, and an encoding. The name is the object ID, which was discussed in the preceding section. The syntax defines the object's data type (for example, "integer" or "string"). A subset of ASN.1 definitions are used for the SMI syntax. The encoding describes how the information associated with the managed object is formatted as a series of data items for transmission on the network. Another ISO specification, called the Basic Encoding Rules (BERs), details SMI encodings.
SMI data types are divided into three categories: simple types, application-wide types, and simply constructed types.
Simple types include four primitive ASN.1 types:
The SMI for SNMPv2 includes two documents: RFCs 1443 and 1444. RFC 1443 (Textual Conventions) defines the data types used within the MIB modules, while RFC 1444 (Conformance Statements) provides an implementation baseline. The SNMPv2 SMI also defines two new branches of the Internet MIB tree: security (1.3.6.1.5) and SNMPv2 (1.3.6.1.6).
SNMP Operations
SNMP itself is a simple request/response protocol. NMSs can send multiple requests without receiving a response. Six SNMP operations are defined:
Figure 3: SNMP v1 Message Format
The version field is used to ensure that all network elements are running software based on the same SNMP version. The community name assigns an access environment for a set of NMSs using that community name. NMSs within the community can be said to exist within the same administrative domain. Because devices that do not know the proper community name are precluded from SNMP operations, network management personnel also have used the community name as a weak form of authentication.
The SNMP PDU has the following fields:
Figure 4: SNMP v2 Message Format
The first part of an SNMPv2 message is often called a wrapper. The wrapper includes authentication and privacy information in the form of destination and source parties. As mentioned earlier, a party includes the specification of both an authentication and a privacy protocol. In addition to a destination and a source party, the wrapper includes a context. A context specifies the managed objects visible to an operation.
The authentication protocol is designed to reliably identify the integrity of the originating SNMPv2 party. It consists of authentication information required to support the authentication protocol used. The privacy protocol is designed to protect information within the SNMPv2 message from disclosure. Only authenticated messages can be protected from disclosure. In other words, authentication is required for privacy.
The SNMPv2 specifications discuss two primary security protocols: one for authentication and one for privacy. These are the Digest Authentication Protocol and the Symmetric Privacy Protocol.
The Digest Authentication Protocol verifies that the message received is the same one that was sent. Data integrity is protected using a 128-bit message digest calculated according to the Message Digest 5 (MD5) algorithm. The digest is calculated at the sender and enclosed with the SNMPv2 message. The receiver verifies the digest. A secret value, known only to the sender and the receiver, is prefixed to the message. After the digest is used to verify message integrity, the secret value is used to verify the message's origin.
To help ensure message privacy, the Symmetric Privacy Protocol uses a secret encryption key known only to the sender and the receiver. Before the message is authenticated, this protocol uses the Data Encryption Standard (DES) algorithm to effect privacy. DES is a documented National Institute of Standards and Technology (NIST) and American National Standards Institute (ANSI) standard.
Originally, SNMPv1 specified that SNMP should operate over the User Datagram Protocol (UDP) and IP. The SNMPv2 transport mapping document (RFC 1449) defines implementations of SNMP over other transport protocols, including OSI Connectionless Network Service (CLNS), AppleTalk's Datagram Delivery Protocol (DDP), and Novell's Internet Packet Exchange (IPX). RFC 1449 also includes instructions on how to provide a SNMPv1 proxy and use of the BER. UDP/IP is still SNMPv2's preferred transport mapping because UDP is compatible with SNMPv1 at both the transport and network layers.
SNMP V1/V2 Coexistence
As a member of the Internet Engineering Task Force (IETF), Cisco is active in defining the SNMPv2 standard. When the standard is final, Cisco will support the SNMPv2 agent in its router software. Cisco routers will then be "bilingual," supporting both SNMPv1 and SNMPv2.
Bilingual support of SNMP gives users optimal flexibility by allowing them to migrate to SNMPv2 on their own timetables. During the period when SNMPv1 and SNMPv2 coexist, Cisco customers will not lose any management functionality. Cisco routers will be able to communicate with both SNMPv1 and SNMPv2 NMSs.
RFC 1452 defines a SNMPv1/v2 coexistence strategy. This strategy defines two basic techniques: a proxy agent and a bilingual NMS. The proxy agent translates between SNMPv1 and SNMPv2 messages. The bilingual NMS incorporates both SNMPv1 and SNMPv2 manager software, and therefore, can communicate with both types of agents. When communication with an agent is required, the manager selects the appropriate protocol.
Cisco's bilingual agent support will work with both the proxy agent and the bilingual NMS coexistence strategies, but neither will be a requirement. Since bilingual agents can communicate equally well with both SNMPv1 and SNMPv2 NMSs, users will not be forced to purchase additional SNMPv2 manager software or proxy agents.
System Monitoring and Management Capabilities
Cisco routers provide many useful system monitoring and management capabilities to help administrators manage large Cisco router-based internetworks. System statistics can be tracked both by interface and by protocol. For example, administrators can query for and receive the number of cyclic redundancy check (CRC) errors on a particular interface or the number of AppleTalk packets sent to or received from an interface. This kind of information is an invaluable component of network baselining (establishing a baseline traffic profile for an internetwork).
Cisco routers also can report a wide variety of information about their internal configuration and status. For example, administrators can ascertain:
With over 450 objects, Cisco's private MIB provides network managers with broad, powerful monitoring and control facilities. Cisco's private MIB supports DECnet (including DECnet routing and host tables), XNS, AppleTalk, VINES, NetWare, and additional system variables that highlight such information as average CPU utilization over selectable intervals. Further, Cisco users can add private extensions to the MIB as required. This capability gives users the flexibility to mold Cisco's SNMP products to their own networks, optimizing management capabilities. Cisco's private MIB tree is shown in Figure 5. This figure expands upon the lower right section of the diagram shown in Figure 2.
Figure 5: Cisco's Private MIB Tree
Cisco also supports other MIBs relevant to router operation. For example, support for some chassis MIB objects allows users to retrieve information about router chassis and installed cards. Card types, card serial numbers, the number of cards in a particular router, the ROM version of those cards, and many other useful variables can be retrieved. Support for the chassis MIB eases network administration. Those responsible for network maintenance can remotely query Cisco routers to quickly discover a router's hardware configuration, thereby saving time and money.
Access Lists for SNMP
Access lists can be used to prevent SNMP messages from traversing certain router interfaces, and therefore, from reaching certain network devices. For example, this feature can be used to prevent other NMSs from altering the configuration of a given router or router group. Access lists are extremely useful in complex internetworks and are implemented across the majority of Cisco's supported protocols.
Multiple Community Strings
For SNMPv1 operation, Cisco permits multiple community strings so that a router can belong to multiple communities. Further, community strings can be either read only or read/write. This feature provides further security by restricting the ability to alter the configuration of Cisco devices.
Traps
Cisco's SNMP implementation allows trap messages to be directed to multiple management stations. This capability allows virtually instantaneous notification of network problems across the internetwork. If, for example, message queue lengths are excessive in one area of the network, management stations throughout the internetwork can be notified immediately.
Cisco provides two extra traps useful in internetwork environments: reload and tty connection-closed. These traps serve to alert network administrators that routers are being reloaded (which, in turn, may indicate more serious problems) and that virtual terminal connections are closing.