Security issues
General security issues
Network security is an important issue in any distributed system.
System and user resources have to be protected from unauthorized use by
other users and by remote applications using methods on local server objects.
In systems utilizing mobile agents, there is also the issue of agent
security. A mobile agent has to be protected from being modified on
its way to fullfil the assigned goal. Otherwise, it may constitute a security
risk to the network and its users.
Cryptography
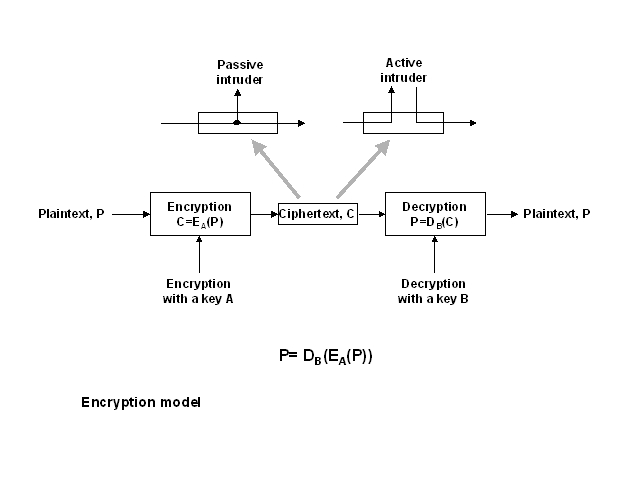
Cryptography is a field of science concerned with encrypting information.
The information, called in the cryptographic jargon plaintext, is
provided as input to an encrypting algorithm. The algorithm uses
certain value, call a key, to generate output, ciphertext.
The ciphertext cannot be read or modified by any intruder, becasue they
do not have the key, which is required to decipher the message. The target
of the transmission uses the same key, or a macthing key, to decrypt
the data.
Secret keys
If there is only one key, then it has to be shared between the source and
the target and it has to remain secret. The sender uses the key in an algorithm,
which produces E(P). At the other end of the communication link the decryption
algorithm using the same key is used to obtain the original message (plaintext
P). If the key is not secret, then anybody, who has access to the key will
be able to read the ciphertext.
It is a simple scheme (although involving very complex encryption algorithms),
but maintaining and distributing secret keys constitutes a problem. Another
problem is that every two parties need a secret key, so a large number
of keys are required to ensure safe communication between any two users.
Public keys
An alternative to a secret key is a pair of keys assigned to every user
of the network. One of them is a public key, which is freely distributed.
The other key is a private key, which is kept secret by the owner.
The keys must satisfy the following equations:
E(D(P)) = D(E(P)) = P
where D and E are encryption algorithms using the keys. They are symmetrical,
so both play a double role: as a encryptor and decryptor. Lets assume that
E is a public key, and D is a private key. Anybody can send an encryted
message to the owner of the private key. It is sufficient to use the public
key to encrypt the message. This will produce E(P), which cannot be read
by anybody but the owner of the private key. When the message reaches the
target, the decryption algorithm using the private key will produce D(E(P))
which is the original plaintext P.
Intrusion
There are plenty of possible intrusions that can compromise the security
of the presented security schemes. We will not discuss them here, because
the goal is to show the basic security concepts and approaches. In most
cases, the intrusion can be prevented by enhacing existing schemes and
algorithms.
Authentication
Authentication is needed to confirm the authenticity of the other party
of the communication session. It is the basis for maintaining Access
Control Lists (ACLs), which protect network resources. Every
user has a predetermined access rights, which are stored in hash tables
with a user id as a key. The user id must be confirmed, so no unauthorized
access is allowed.
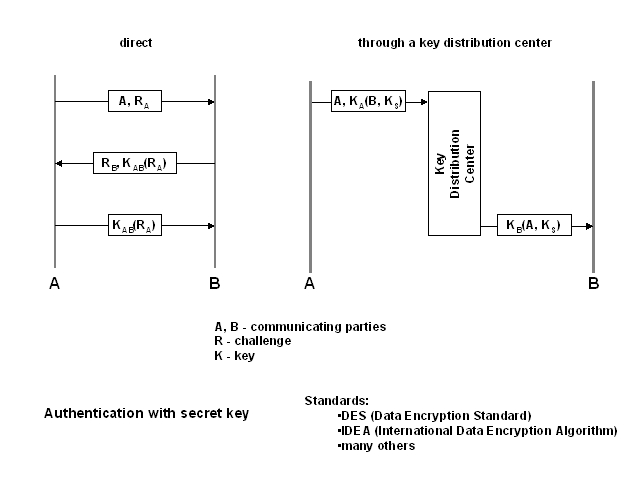
Secret keys
Secret keys can be used to confirm user's authenticity either through a
direct communication or through a Key Distribution Center (KDC).
To be identified, the user A sends its identity to the access granting
authority. In the examples, both sides of communication are authenticated,
so the first message includes also a challagenge for the other side. The
user B uses the shared secret key to encrypt the challenge, which authenticates
B from A's perspective. B includes also a challenge for A. A encrypts the
challenge and sends the encrypted message back to B. B can confirm that
the challenge has been encrypted using the secret key, so it could come
only from A.
The scheme with a KDC depends on a center that everybody trusts. In
this case, a secret session key can be established for every secure session.
The user A sends to the KDS the id and encrypted id of the target and a
proposed key for the session. This encryption uses a key that only A and
the KDS share, so the KDS is assured that it is A, who sent the message.
The identity of the target is decrypted, so B can be contacted. A key shared
by the KDC and B is used to encrypt a message containing the identifier
of the source and the proposed session key. Only B can decipher this message,
so both ends are assured to be A and B.
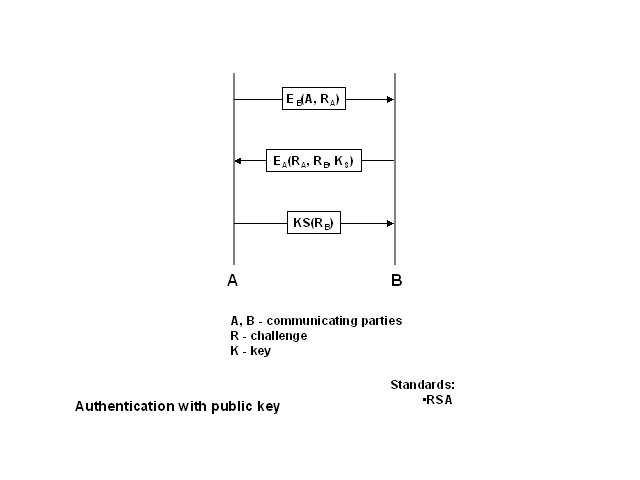
Public key algorithms
Public keys can also be used for authentication. In this case, the initiating
party uses the public key of the targeted party to encode A's identity
and a challenge for B. Only B can decode this message using the matching
private key. After doing so, B applies an encryption algorithm with the
public key of A to send back a message with the challenge sent by A, a
proposed session key and a challange for A. Again, only A can decode this
message using the matching private key. It then sends back an encrypted
value of the challange received from B. This assures B that the communication
is indeed with A.
Digital Signatures
Digiatl signatures are used as proofs of authenticities of received messages.
A sender of a message signs the message, so the recipient can store it
as a proof that a message indeed came from the sender. It is very important
in online shopping, banking, etc. It is an equivalent of a hand-written
signature, which people use to authenticate documents.
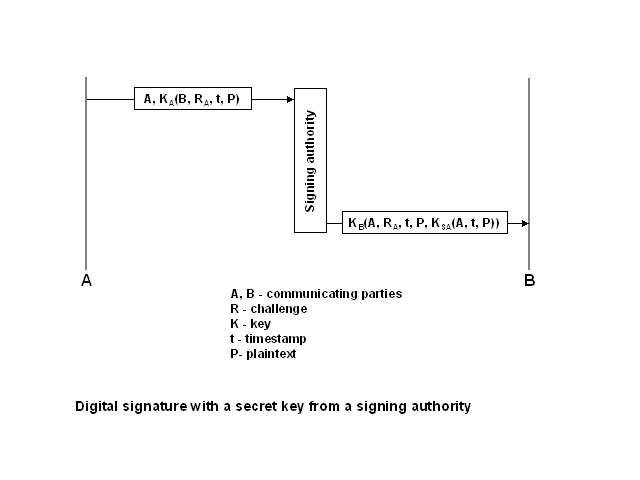
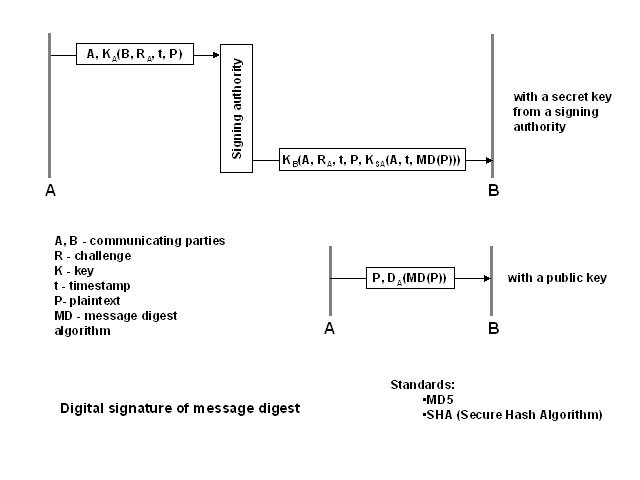
Secret keys
The scheme with secret keys involves a signing authority (SA),
which is analogous to a key distribution center. The user A sends the identity
and encrypted message with the identity of the target, the challenge for
B, a timestamp and the plaintext. A secret key shared by the SA and A is
used, so the SA knows that the message comes from A. It obtains the details
about the target of the message and uses appropriate secret key (shared
with B) to encrypt a message containing the identity of the source, the
challenge, time stamp, plaintext and another part, which is encrypted using
the secret key, which belongs only to the SA. This part includes the source,
timestamp and the original message. B can use this as a proof of receiving
the message from A. The SA has to be involved in such confirmation, because
the proof has been signed by a secret key that the SA does not share with
anybody.
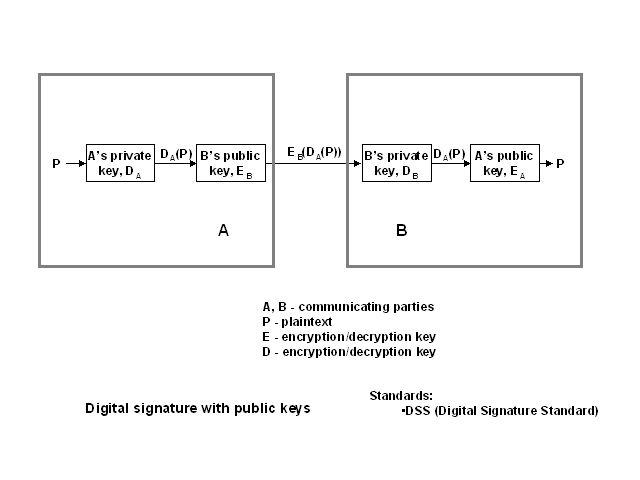
Public keys
A private key can be used to sign a message. This scheme does not require
a presence of a trusted intermediary (SA). The message is encrypted using
a private key of the source (A). Then, the the encryption algorithm is
applied once more, but this time the public key oof the target (B) is used.
The doubly encrypted message is sent over the network to the target. It
is encrypted using B's public key, so only B can decrypt it with the matching
private key. The output of this process is saved as a proof of authenticity
of the source. Only A knows its private key, so nobody else could have
produced a message encrypted with that key. A public key of A can be used
to both obtain the original message and to prove that the encrypted message
originated at A. Applying A's public key to something that was not produced
by A would certainly end up with a garbage rather than the message in question.
Message digests
Frequently, a message, which is being digitally signed does not need to
be encrypted. It may save plenty of time, especially for long messages,
because encryption and decryption algorithms are very complex and time
consuming. In such a case, a message digest can be used. A message digest
is a value, which is obtained from a message by a special hashing algorithm.
Producing a message digest of a message is much faster than encrytping
the message. The message digest algorithms ensure that the value of the
digest can be obtained uniquely from any message. If that is so, then it
is sufficient to sign the messgae digest to ensure the authenticity of
the sender.
Bothe secret keys and public/private keys can be used to sign message
digests. It is sufficient to use a message digest in place of the plaintext.
Of course, the plaintext has to be included as well, because there is no
way to obtain the original message from its digest.
Java security facilities






